Bypassing NAT: Exposing your entire network over the Internet
In my previous article about Bypassing NAT, I discussed tunneling programs to allow you to access a port from outside the network, such as Tor, ngrok, and more. But what if you want access to your entire network remotely? Not the best security-wise but extremely convenient for things like software development.
Proxy
One way this is done is through a reverse proxy. More information can be found here, which says
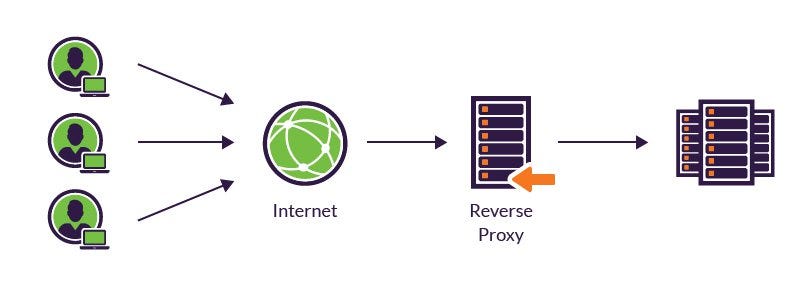
A reverse proxy server is an intermediate connection point positioned at a network’s edge. It receives initial HTTP connection requests, acting like the actual endpoint.
In this case, we use it to access our home network, by redirecting requests from the client device anywhere in the world (with internet access) through the server, to the home network. I currently use microsocks, a simple SOCKS5 proxy server.
To connect to the server, I either use
proxychains4for Linux, make sure to edit/etc/proxychains.confunder[ProxyList]- SocksDroid, which turns the proxy server connection into a VPN, tunneling all your internet connections through it.
I got the idea of this from using Burp Suite since that requires a proxy to intercept all the connections.
VPN
I have not experimented enough with this, but it is theoretically possible. Some examples would be something like the VPN connections in TryHackMe/ HackTheBox to connect you to the network of machines.
You could set up a local VPN server and test. A sample resource is listed below. (not tested by me yet)
Things to take note of
- These only allow a network to be accessed through a single network service of one port. You still need
- If you didn’t know, these services make accessing your network slower. Only use them to access your internal network, and not leave your device connected to the VPN/ Proxy to access the internet.
Overall
I think this is useful, especially for things like setting up a home server (which I am still doing as of the time of writing).